How to Turn Your Home Office into Fort Knox
By Rebecca Christoforidis
Published October 13, 2023
There’s no place like home. It offers both safety and security, except when it comes to the dangers of cyber threats.
With the increase in remote work, the increase in fraudulent emails, spam and phishing attempts through corporate accounts has risen dramatically. Cyber threats have grown in number and in sophistication and frequency. Protecting your home office from these threats is crucial for ensuring the safety of your work and personal information. In this blog post, we will provide valuable tips on keeping your home office safe and secure from cyber threats.
Common Cyber Threats
Keeping track of the sheer number of cyber threats making the rounds is a daunting task. But to protect your home office, it’s important to at least know the ones that are most common.
Spear Phishing
According to imperva, 3.4 billion spam emails are sent every day. They are intended to deceive the recipient into taking actions that will compromise their personal information, financial data, or security. You may receive an email that appears to be from a trusted source, such as a supervisor, a bank, or a vendor. It may ask you to click a malicious link, download harmful attachments, or provide sensitive information such as usernames, passwords, and credit card details.
Example of a Phishing email
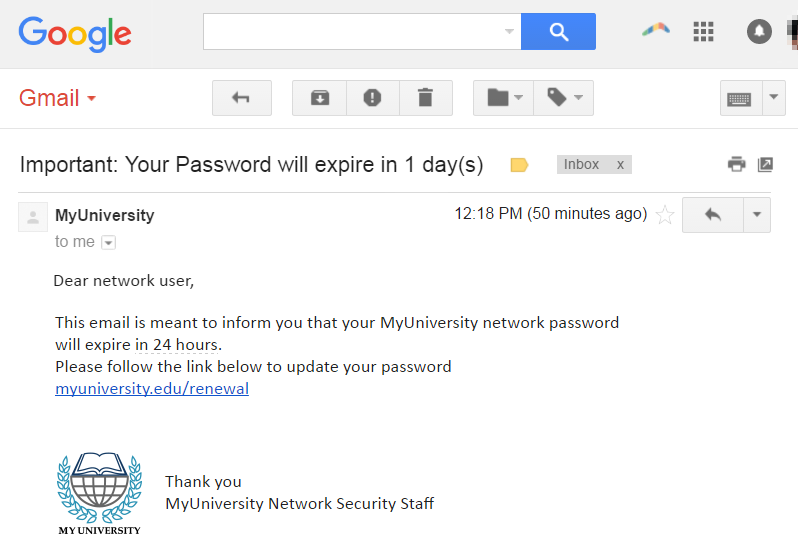
Source: imperva
Common characteristics of phishing emails:
- Spoofed Sender Information: Phishing emails often appear to be sent from a legitimate source or organization. The sender's name and email address may be forged to make it seem like a trustworthy entity.
- Threats: Phishing emails often try to incite fear and urgency in the recipient, prompting them to take immediate action. Threats include account suspension, legal action, or other consequences.
- Suspicious Links: Phishing emails contain links that direct recipients to fake websites designed to mimic legitimate sites. These sites are used to collect login credentials or other personal information.
- Malicious Attachments: Some phishing emails include attachments, which, when opened, can infect the recipient's device with malware or ransomware.
- Request for Personal Information: Phishing emails often request sensitive information such as login credentials, Social Security numbers, credit card details, or other personal data.
- Misspellings and Grammar Errors: Many phishing emails contain spelling and grammar mistakes, which can be a red flag.
- General Greetings: Using things like “dear user” instead of the recipient’s name can be an indication of a phishing email.
To protect yourself from phishing emails, always verify the sender, don’t click on suspicious links, don’t open suspicious attachments, always verify requests for information, use email filters, and keep your software updated.
Malware
Malicious software, such as viruses, ransomware, attackers, and trojans, can infect your home office devices if you accidentally download or execute a malicious file or visit compromised websites. They can steal your data, disrupt your system, encrypt your files, and demand a ransom to “free” them, and propagate by spreading and infecting more devices. And these are just a few of the ways they can harm your system.
Right now, the malware that is circulating is called AVrecon. It is targeting home office routers and. to date, has infected more than 70,000 machines in 20 countries.
In order to protect your home office against malware, it's crucial to use security software, keep your operating system and software up to date, be cautious of unsolicited email attachments and links, and practice safe browsing habits along with constant internal training and auditing.
Weak Passwords
Using weak, insecure, or recycled passwords for your home and Wi-Fi network will make you an easy target for cybercriminals. It will also negate any software protection tools you employ, such as firewalls or VPNs. You should avoid using information such as birthdays or other easily guessed information.
Protection Measures
Positive steps you can take to ensure your password passes muster include using a password manager to securely store and generate passwords, as well as WPA3 encryption to further bolster your security.
You should also consider enabling multi-factor authentication (MFA), which is a security mechanism that requires two or more forms of identification or authentication to access an account, system, or application. The most common factors used in MFA are:
- Something You Know: Most often, a password or a Personal Identification Number (PIN).
- Something You Have: Physical objects such as a smart card, security token, or a smartphone. A one-time code sent to your phone via SMS or generated by an authentication app like Google or Microsoft Authenticator, or Authy.
- Something You Are: This involves biometric factors like fingerprints, facial recognition, or retinal scans.
To keep your Wi-Fi network safe, use a strong and complex password that mixes letters, numbers and special characters. You should also change your default router login credentials and routinely update the router firmware to patch security weaknesses that hackers can exploit.
Antivirus Software
Antivirus software is essential for a strong firewall, and most organizations will provide a robust tool for their employees. However, if yours does not, or if you’re looking for a basic solution to protect your PC or laptop or a highly advanced protection capable of shielding your devices from viruses, hacker attacks, and fraud, there are many products available that can do the job.
Practice Safe Online Behavior
It’s best to avoid unknown and uncertified sites. If your firewall is blocking you from a site, it’s probably doing so for a good reason. You should also avoid sharing sensitive personal information, unless necessary and be cautious about what you share on social media and with whom, as it can be used to exploit you.
You may want to consider securing your home office by locking it when not in use. Store physical documents and devices containing sensitive information in a locked drawer or safe. And keep personal and work devices separate. Always report unauthorized activity or access immediately to your IT department or whoever oversees your cybersecurity countermeasures.
Backup important files and data regularly to an external device or a cloud-based service. In case of a cyberattack or data loss, having backups will help you recover your data.
Educating yourself (and your family) about the importance of cybersecurity can ensure that everyone in your household follows safe online practices.
Cybersecurity is an ongoing process that requires you to remain vigilant and ready to adapt to new threats as they emerge. By implementing these cybersecurity measures, you can significantly reduce the risk to your home office. Protecting your home office not only safeguards your work but also your personal information, giving you peace of mind as you continue to work from home.